What Is A Network Security Key?
The community safety key's a form of community password or the passphrase in the shape of bodily, virtual signature or biometric records password this is used to provide authorization and Check this accessibility to the wi-fi community or device on which the consumer requests to hook up with.
The protection key also provisions to set up a at ease connection among the soliciting for customer and the serving network or wireless tool like routers and so forth. These protect our community and gadgets from unwanted get right of entry to.
The safety key is of various sorts and is widely used everywhere in our daily services like on line banking, cash transactions in the form of OTP’s (one time password), on-line shopping, having access to the Internet carrier, login into the mail account or any network tool etc.
Types Of Network Security Key
The maximum commonplace varieties of a community protection key that are used for authorization in wireless networks consist of Wi-Fi blanketed get right of entry to (WPA and WPA2) and stressed equal privacy (WEP).
#1) WEP
WEP makes use of a 40-bit key for encryption of the facts packet. This key is combined with a 24-bit IV (initialization vector) to make an RC4 key. This 40 bit and 24 little bit of IV makes a 64-bit WEP key.
There are two types of authentication methods used i.E. Open gadget and shared key authentication.
In the open device authentication method, the asking for purchaser host want now not present the credentials to the get entry to point for authentication as any consumer can try and accomplice with the network. Here, handiest the WEP key's used for the encryption procedure.
While in the shared key authentication, the WEP key is used for authentication by deploying a 4-way venture-reaction handshake system.
Firstly, the host consumer sends the authentication request to the access factor. Then the get right of entry to factor in reaction sends again the clean-text mission. By using the WEP key, the client host will encrypt the task text and send it returned to the get entry to factor.
The response will then be decrypted via the access factor and if it's miles equal to the task textual content, then it'll transmit a high quality reply. Later the authentication and the affiliation method will get completed and again the WEP key's used for encryption of the data packets the usage of RC4.
From the above method, it appears that evidently this technique is a relaxed one, however nearly the important thing can effortlessly be decoded by means of every person via cracking the project frames. Therefore, this approach of encryption and authentication is much less in practice and the WPA that's a extra comfortable method than this has been advanced.
#2) WPA and WPA2
The host device which desires to connect to the network calls for the safety key to begin the communication. The WPA and WPA-2 each work on the precept that after the validation of the key, the exchange of records most of the host device and the get entry to factor is in an encrypted form.
The WPA deploys a temporal key integrity protocol (TKIP) which uses a consistent with- packet key because of this that it dynamically produces a sparkling 128-bit key on every occasion whilst a packet arrives and allocates the same to the information packet. This saves the packet from any undesirable get admission to and assaults.
It does have a message integrity check, which guards the data towards the viruses that could regulate and re-transmit the packets in step with themselves. In this manner, it replaces the cyclic redundancy take a look at technique for errors detection and correction that became used by the WEP.
WPA and WPA-2 -Personal (WPA-PSK): This is used for domestic networks and small-scale workplace networks as it doesn’t want the server primarily based authentication. The data is encrypted by way of extracting the 128 bit key from the pre-shared key of 256 bit.
WPA and WPA2 Enterprise: It deploys the 802.1x authentication server and RADIUS server authentication that's a much cozy one and is already described in detail in our previous tutorials for encryption and get admission to. This is particularly used in authorization and authentication techniques of the commercial enterprise agencies.
How to Find Network Security Key for Router?
The network safety key performs a totally crucial position in connecting your devices to the router on the way to get admission to the Internet.
If the network security key is altered by means of a person or if you overlook your community protection key, then you will now not be able to get right of entry to the Internet services like browsing on the net, looking movies online or gambling video games on-line and so forth.
How and where to the find network safety key on the router:
The router’s community security secret's categorised on the hardware and is marked because the “ safety key”, “WEP key”,” WPA key” or “ passphrase”. You also can derive it from the manual that includes the router while you purchase it.
You can also learn the Network protection key of the router by logging in into its default settings on its web interface.
Security key for Router
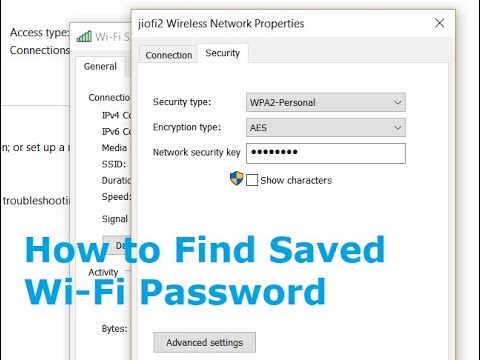
How to Find Network Security Key for Windows?
The network protection key for the Windows PC or laptop is the WI-Fi password to connect with the Internet community.
I am using windows 10, so the steps to be followed to go into the community security key or password are as follows:
Go to the begin menu and pick the settings alternative, after that pick the network and Internet option and visit the Network and sharing middle.
In the community and sharing center, pick out the name of the community on that you want to connect with, and then within the Wi-Fi status, pick the wi-fi houses.
In the wireless community houses, pick the network protection key alternative and input your password and then input the next button. After checking the network necessities and after acquiring the IP cope with, you will be linked to the internet.
Now you'll get related with the Internet community and then it'll display as related. You can also take a look at the residences, by means of clicking on the button.
By using this site you agree to this Privacy Policy. Learn how to clear cookies here
Germany Amateur Regionalliga West Sing meinen Song: Die Musik des Herzens baixar 1win e35dkz thidaihocbrandscom Rikvip Headache Treatment PARTIDO EN VIVO UD Montijo VS CP Cacereño PARTITA IN DIRETTA Venezia VS Lecce MATCHDAY - Cittadella vs Monza